When we buy smartphones today, we are always concerned with the material quality, the number of cameras, and the design. However, cybersecurity experts advise that we should get worried about the device’s security and data privacy over all other things.
That’s where the untraceable Phone comes into role. We can bet that mobile security is a real issue, and certain manufacturers are concerned about protecting the data stored on their devices, hence manufacturing untraceable phones.
We have compiled a list of the best untraceable prepaid cell phone options that are unhackable and feature utmost safety.
The guide also outlines a step-by-step guide to easily make your cell phone untraceable.
Table of Contents
What is an Untraceable Phone?

If you’re an agent or a former POTUS who was eavesdropped on by the NSA, you’ve probably heard of the Blackphone – the so-called “hacker-proof” smartphone. An untraceable handset puts the user’s privacy back in their hands.
Unlike free government phones, Blackphone is the first privacy-focused smartphone designed in response to extensive NSA spying accusations and global surveillance impositions.
The pre-installed privacy and security software, which protects your identity and hides your activity, is at the heart of the Blackphone suite.
Untraceable phones follow the same approach as incorporated into Blackphones and keep your data safe and secure.
It assures that nobody will hack your information, and you are safe from a data breach or any other similar concerns.
Why Do You Use Untraceable Phones?
Someone could want to remain anonymous for a variety of reasons. Perhaps you’re calling an employer with an anonymous tip.
Instead of giving out your primary phone number, you might want to utilize a secure messaging service like Signal or Telegram.
Perhaps you’re attempting to avoid giving up your primary phone number to marketers who would almost certainly call you after you’ve viewed a real estate listing or requested insurance quotations.
You could use an untraceable burner phone or a SIM to protect your identity. You can use the number without risk of being identified if you can get a handset or SIM card that get not tied to your real-world identity.
Burner phones have limited capabilities because they are featured phones. They offer the best battery life, thanks to their small weight.
Most people don’t have access to cameras or a current browser, so they rely on phone calls and text messages. Many of these devices can run for days, if not months, on a single charge.
Unlike Linux phones, Burner cellphones are suitable for use in an emergency. Because they can be charged and turned off until needed, they get frequently seen in emergency survival kits.
It’s a spare phone with a lengthy battery life that doesn’t require an expensive cell phone plan.
10 Best Untraceable Phones You can Buy in 2022
Are you ready to take a deep dive into the list of the best untraceable phones? Check them out here!!
Here’s a complete guide to the best options worth adding to your collection.
1. Blackberry DTEK50 STH 100
Pros
- Photo Quality is Stunning
- 2TB microSD card support
- Access to Google Play apps
Cons
- Battery life is limited.
The Safest Android Phone, the Blackberry DTEK50 STH 100, is a worthy addition to your cart.
DTEK50 assures that you have complete control over how you share personal information, such as your location, photos, and texts. Not all cell phones are built the same when it comes to security.
With DTEK50, you’ve got built-in protection for your sensitive data, making this model the best untraceable prepaid cell phone. It has an 8MP front camera and a 13MP auto-focus rear camera.
2. Silent Circle Phone
Pros
- Encrypted and verified from beginning to end
- There is no new hardware needed.
Cons
- None
Silent Phone ensures that your discussions are secret, and you get only connected to the people you want. The entire encryption process takes place on the device. No one is allowed to listen in.
This untraceable Phone allows your team to communicate securely over the internet while being simple to set up and use.
Silent Phone is simple to set up and administer, and there is no need for end-user training. It may be deployed via MDM and supports SSO and SIEM systems.
This does not require any additional hardware, which is an added plus.
3. Sirin Labs Finney U1
Pros
- Secure hardware wallet
- Fingerprint-resistant oleophobic coating
- Dual MCU architecture
- Firewall protection
Cons
- The wallet is offline.
The FINNEY runs on SIRIN OS, which has a superb Security Suite Layer, an Embedded Cold Storage Wallet, a Token Conversion Center, and Sirin’s dCENTER, which showcases the finest of DApp nation.
The phone features a 12 MP primary camera and an 8 MP selfie camera with a 74-degree diagonal viewing angle.
It has 128GB of eMMC storage, 6GB of LPDDR4 RAM, a 2T SD memory card slot, Android 8.1 with SIRIN OS 3.01, Qualcomm Snapdragon 845, Adreno 630 GPU, and Hexagon 685 DSP.
Download the untraceable phone app for Android and iOS to make your Phone safe and secure.
4. FINNEY

Pros
- Modern & Exclusive Design
- Ultra-Fast & Smooth Usage
Cons
- None
Finney’s modern and exclusive design is what makes this untraceable Phone worth adding to your list. It has 128 GB of inbuilt memory, which can get upgraded to 2 TB.
Modern sports automobiles served as inspiration. The untraceable phone tracking feature allows you to keep your Phone’s data safe and secure.
At the software and hardware levels, it used military-grade blockchain technology.
Furthermore, experts claim that it includes an internet-free Bitcoin wallet, making it suitable for cryptocurrency investors.
5. Sirin V3

Pros
- Encrypted storage on boot
Cons
- Disallow apps installation
- Inappropriate Voice recording
Sirin V3 uses a multi-layered cyber security suite, including a behavioural-based and machine learning Intrusion Prevention System (IPS).
It provides a proactive real-time cyber defence. Sirin V3 is based on Samsung’s most recent business-class devices and includes a multi-layered platform embedded into the hardware and software.
The secure platform regularly verifies the device’s integrity through a chain of security checks that start at the hardware level and continue to the operating system and detects any tampering to ensure your data is always safe.
6. Blackphone Privy 2.0
Pros
- Triple password protection
- Trusted updates
Cons
- None
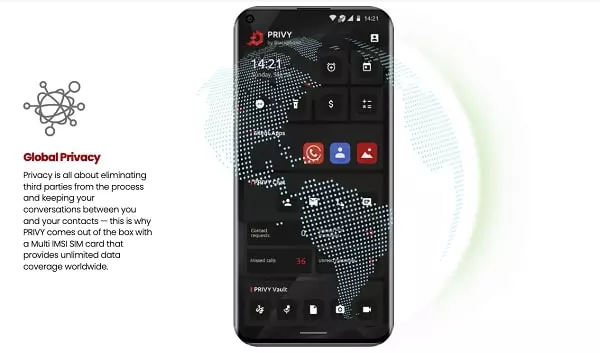
The Blackphone PRIVY uses cryptographic protocols to encrypt your connection so you may send and receive ZRTP instant messages and make VoIP conversations without worrying about your privacy.
This untraceable Phone allows you to safely make and receive calls, instant chats, and file sharing (up to 100MB files) with other Silent Phone users, regardless of their device.
PRIVY comes packed with state-of-the-art programs for encrypted communications and file storage – PRIVY Chat and PRIVY Vault to provide privacy of communication and absolute data protection.
Each application uses end-to-end encryption to protect data in transit and securely stores data at rest in encrypted databases.
7. Bittium Tough Mobile 2

Pros
- Tamper-proofed to prevent data theft
- Trusted boot
- Multi-microphone active noise cancellation
Cons
- None
A secure device that is developed for those who require maximum security. The best part is that it is impossible to hack; hence is commonly employed by security agencies in over 30 nations due to its high requirements.
With multi-layered protection built into the Bittium Tough Mobile 2 smartphone’s hardware and software, you can keep your data safe.
Complement the smartphone with Bittium Secure Suite device management and encryption software for complete end-to-end mobile security.
It offers a hardware-based privacy mode that turns off microphones, cameras, and Bluetooth while lowering sensor sensitivity.
8. Bittium Tough Mobile 2 C

Pros
- Dual-boot device
- Highly secure
Cons
- None
The Bittium Tough Mobile 2 C smartphone with Bittium Secure Suite device management and encryption software for government agencies and authorities delivers the highest privacy and security.
Bittium Secure Suite, which must get purchased separately, expands from tens to thousands of users and requires the installation of client software and a back-end server.
It is an innovative software suite with a full range of services for secure communications. It is always required by Bittium Tough Mobile 2 C.
The Dual-booting feature allows you to run two completely different operating systems on the same device while keeping all of your data separate.
9. IntactPhone Arcane

Pros
- Minimized cyber-attack surface to the extreme.
- Fused defence and control application ensures the safe use of corporate devices.
Cons
- None
An ideally designed for top business people and detective agents, this Phone ensures their data gets never leaked.
It allows users to download and install programs that have been certified by a community security firm.
IntactPhone is the most secure untraceable burner phone for businesses in the world. It is used to aid in the prevention of both hacking and tracking.
This network got sponsored across Asia, Europe, Israel, the United States, and Latin America.
10. IntactPhone BOND

Pros
- Threat detection
- URL Classification
- Encrypted data
Cons
- None
It is a system built from the ground up to protect against all cybercrime, making it the best online security and privacy option.
Its network covers China, Japan, Canada, Israel, EMEA, APAC, Mexico, and the United States.
It has a mobile security platform that brings together the finest of everything.
The IntactPhone offers security and privacy by using ZRTP to encrypt voice-over-IP calls.
To detect evasive assaults, IntactPhone detects behaviour-based anomalies across Wi-Fi connectivity, cell tower connectivity, and applications.
How to Make Your Cell Phone Untraceable?
Wondering about how to make your cell phone untraceable? Here’s a comprehensive guide to making your Phone untraceable.
- First, you need to purchase a pre-paid phone without GPS to avoid tracking.
- Secondly, do not complete the rebate form, as all your personal information will be entered into searchable databases and sold to third parties.
- Give your cell phone number only to those you trust. Never put your phone number on a blog, social networking site, or another public forum. Use your work phone number if you have to offer a phone number for an application or paperwork.
- Refuse to be tracked down using GPS-enabled phones.
- Make use of a business card. Even if you have automatic call blocking enabled, your cell phone number may appear on other people’s phone bills. To avoid this, get a calling card and follow the instructions on the card while making phone calls. Calling cards are widely available at supermarkets and convenience stores.
Our Thoughts
That’s all about it. We hope you have found the guide informative. Your ISP and other websites keep track of everything you do on the internet.
Hence, using the best unhackable Phone or untraceable Phone from any top manufacturer should provide encryption and privacy in stock form.
So, what keeps you waiting for now? Get any of these untraceable cellphones now and enjoy safety to the maximum extent.
Last update on 2025-04-06 / Affiliate links / Images from Amazon Product Advertising API





